Authentication in Citrix ADC (NetScaler) is done from BSD, not from Citrix ADC (NetScaler). Because of this, traffic usually originates from NSIP. This is sometimes of surprise to network (and firewall) admins.
It usually comes means: It may very well be a little bit different.
Normal behaviour
Usually NetScaler sends an authentication request to BSD. The AAA daemon in BSD will then connect to the authentication source, authenticates the user and replies with a success or failed message to NetScaler OS. As NetScaler’s BSD is not able to do network communication other than via NSIP (NetScaler IP), therefore authentication traffic will always origin from NSIP. This is very different from usual Citrix ADC (NetScaler) behaviour: All the rest of traffic will come from a SNIP (Subnet IP).
This is true under following circumstances:
- There is a route from NSIP to authentication source (costs > 1 are not honoured)
- There is no direct route from a SNIP
Using a network profile will not change anything, as network profiles won’t affect NSIP traffic.
Load balanced deployment
In my opinion it’s always best practice to load balance authentication traffic. There are reasons for this:
- It’s not possible to specify more than one authentication server per server definition.
- Authentication will fail, if authentication source is down. So the policy got a single point of failure in it.
There are two work around: a bad and a good one.
- The bad one: Using more than one policy, pointing to the same directory. Why is this bad? This will double the numbers of false logons, in case a user uses a wrong password, as Citrix ADC (NetScaler) will test both policies (but both will fail as they authenticate to the same directory). In this case, traffic will come from NSIP (NetScaler IP).
- The good one: Load balancing the authentication servers. The server definition will point to the load-balancing vServer, because of this we need not more than a single policy. Again authentication traffic will come from NSIP, but flow, internally, to the vIP of the load-balancing vServer. The service – like any load-balancing service – will use the SNIP (Subnet IP) for back-end connection. This is just normal load-balancing traffic.
No route from NSIP
All this is not true if there is no route from NSIP to the authentication source, but from a SNIP only. In this case, Citrix ADC (NetScaler) is forced to use a SNIP. Which one? It is a normal routing decision. It behaives like all other Citrix ADC (NetScaler) functions.
If there are more than one SNIP in the selected subnet, these SNIPs get load balanced, just like any other Citrix ADC (NetScaler) traffic.
Forcing traffic to an IP other than NSIP (aaadnatip)
If there is a reason for you to not allow traffic coming from NSIP, but you have to force traffic from a certain IP, there is a chance to use an IP different from NSIP. But it is not possible to use an SNIP. Instead you may force traffic to a so called aaadnatIp. This aaadnatIp has to be an IP different from all other IPs on this NetScaler. There is a description from Citrix available (see CTX132935 CTX218050).
Setting a aaadnatip
This is done via command line:
set aaa parameter -aaadnatIp <ip-address>
It can also be done from GUI in Security → Change global settings. The parameter here is called NAT IP Address.
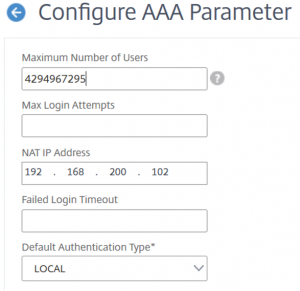
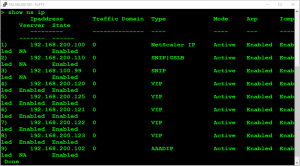
a show ns ip will result in this output:
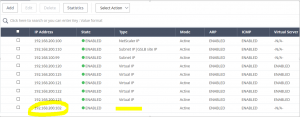
Output from GUI (system → network → IP)
I hope I could clarify things by a little bit. Drop me a message if you find my post useful. Cheers
Johannes

But what about monitoring the servers in the service group? This traffic still comes from the NSIP…
Sure, you’re right.
What is the Citrix ADC (NetScaler) ?
It is a little bit like a snow man, but also like a dragonfly and a Rols Royce. But more like a tiger shark than like a Rols, to be honest. Compare it to an intergalactic pudding?
Maybe you rather spam some other blogs?
By the way: I removed your link. Maybe I’m stupid. But not that much.