 last update: September 25th 2019
last update: September 25th 2019
I was recently asked: Johannes, is it possible to orun the same AAA server, from the inside with single factor, from the outside with two factor authentication?
Of course it is. That’s how you do:
Prerequisites
My test environment contains of a lb vServer (lb_vsrv_colors). I created a AAA vServer aaa_multifactor_ath. There is a content switching vServer, cs_vsrv_auth-test.
There is an AD domain (training.lab) and a RADIUS server. Internal users should only authenticate to training.lab, while extrenal users will have to authenticate to both, RADIUS and LDAP.
creating the prerequisities
I don’t go into this, I just type the commands here. I assume, you’re able to create servers like that.
Citrix ADC LB vServer
add service svc_red 192.168.30.10 HTTP 80
add service svc_green 192.168.30.11 HTTP 80
add service svc_green 192.168.30.12 HTTP 80
add lb vserver lb_vsrv_colors HTTP 0.0.0.0 0 -persistenceType NONE -cltTimeout 180
bind lb vserver lb_vsrv_colors svc_red
bind lb vserver lb_vsrv_colors svc_blue
bind lb vserver lb_vsrv_colors svc_green
citrix ADC AAA vServer
add authentication vserver aaa_multifactor_auth SSL 0.0.0.0
bind ssl vserver aaa_multifactor_ath -certkeyName training.lab_wildcard_cert
Citrix ADC CS vServer
add cs action cs_act_aaa -targetVserver aaa_multifactor_auth
add cs policy cs_pol_AAA -rule "HTTP.REQ.HOSTNAME.EQ(\"aaa.training.lab\")" -action cs_act_aaa
add cs vserver cs_vsrv_auth-test SSL 192.168.200.240 443 -cltTimeout 180
add cs action cs_act_aaa -targetVserver aaa_multifactor_auth
add cs policy cs_pol_AAA -rule "HTTP.REQ.HOSTNAME.EQ(\"aaa.training.lab\")" -action cs_act_aaa
bind cs vserver cs_vsrv_auth-test -policyName cs_pol_AAA -priority 100
bind cs vserver cs_vsrv_auth-test -lbvserver lb_vsrv_colors
set ssl vserver cs_vsrv_auth-test -ssl3 DISABLED
That’s all the requisites. So we have a content switching vServer, sending all traffic to a load balancing vServer, except of traffic going to aaa.training.lab. This gets sent to the aaa vServer.
LDAP profile
There also is a LDAP profile. I’m using default policies only
add authentication ldapAction auth_LDAP_prof -serverIP 192.168.30.10 -ldapBase "dc=training,dc=lab" -ldapBindDn LDAP@training.lab -ldapBindDnPassword Top_Sectret_Password -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn
192.168.30.10 usually would be a load balanced vServer. my domain is training.lab, my “administrative bind DN” is ldap@training.lab, password Password1.
Authentication
There will be 2 authentication policies, one of them will be LDAP, one for Radius. Unfortunately I didn’t have a RADIUS server, so I’ll use local authentication instead.
I need 2 LDAP policies: A policy for singe factor, used for clients connecting from local LAN, and a second one for all the rest. Local LAN is 192.168.200.0/24.
Authentication policy for local LAN

add authentication Policy auth_LDAP_pol_LAN -rule "CLIENT.IP.SRC.IN_SUBNET(192.168.200.0/24)" -action auth_LDAP_prof
As you see: This policy will only authenticate users, connecting from local LAN.
Authentication policy for 2 factor
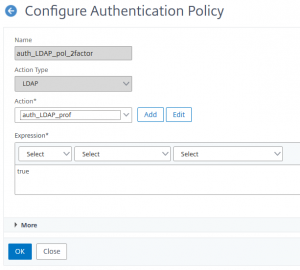
add authentication Policy auth_LDAP_pol_2factor -rule true -action auth_LDAP_prof
This is the default policy, a typical “and all the rest …” policy. But wait, what about n-Factor, this is just a single factor, isn’t it?
Well, that’s true. I will do cascading n-factor authentication. There will be a second authentication screen, looking for the RSA token (in my case: for the local password on Citrix ADC / NetScaler)
The “RADIUS” policy
as mentioned above, I don’t have a RADIUS server, so I won’t do RADIUS, instead local authentication.I hope you know how to do RADIUS actions. In case you don’t: ask Carl Stalhood
I created a AAA user on NetScaler with the same name as the LDAP user has.
add aaa user contractor1 -password 1234
I just need an authentication policy.
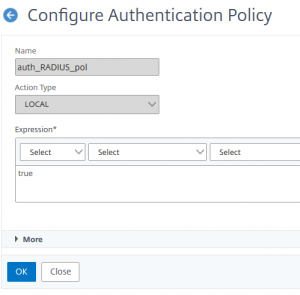
add authentication Policy auth_RADIUS_pol -rule true -action LOCAL
That’s, of course, not enough. We will also need a logon dialogue, a login schema, for the second factor. This can be found under Security → AAA Authentication Traffic → Login Schema.
 We add a new login schema
We add a new login schema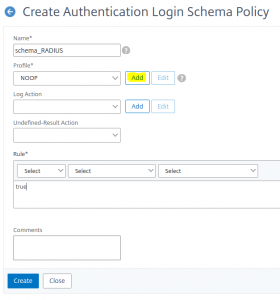 This login schema needs a new login dialogue. It is called the profile.
This login schema needs a new login dialogue. It is called the profile.
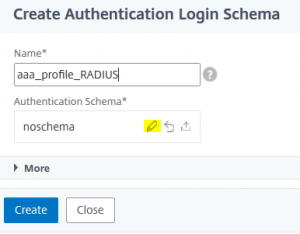 give a name to your profile and click the pen next to noschema
give a name to your profile and click the pen next to noschema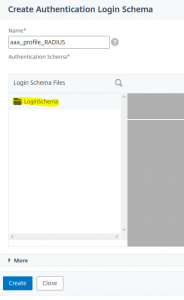 enlarge Loginschema
enlarge Loginschema
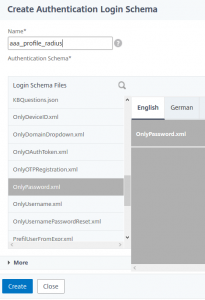 select OnlyPassword.xml
select OnlyPassword.xml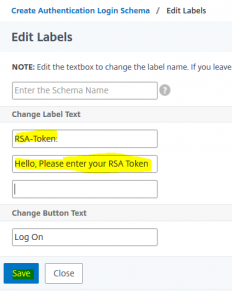 do all chenges required (for all languages required) and click save
do all chenges required (for all languages required) and click save This created a new schema. You may find this schema’s XML file in /flash/nsconfig/loginschema.
This created a new schema. You may find this schema’s XML file in /flash/nsconfig/loginschema.
The Policy label
A policy label is a punch of policies. In this case, these are authentication policies.
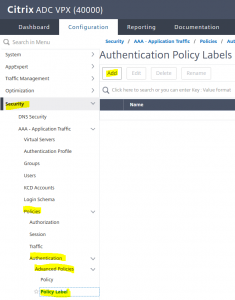 From Security → AAA – Aplication Traffic → Policies → Authentication → Advanced Policies → Policy Label click New.
From Security → AAA – Aplication Traffic → Policies → Authentication → Advanced Policies → Policy Label click New. 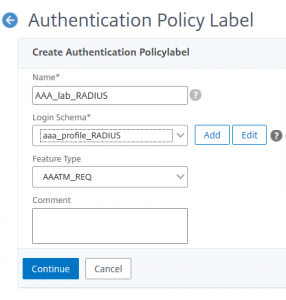 Give this new policy label a name, bind your login schema (created before) to it. Click Continue.
Give this new policy label a name, bind your login schema (created before) to it. Click Continue.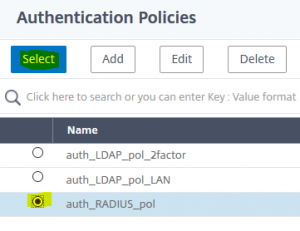 Select the RADIUS Policy
Select the RADIUS Policy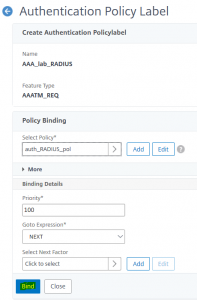 Bind the radius policy. No more policies needed.
Bind the radius policy. No more policies needed.
add authentication policylabel AAA_lab_RADIUS -loginSchema aaa_profile_RADIUS
bind authentication policylabel AAA_lab_RADIUS -policyName auth_RADIUS_pol -priority 100 -gotoPriorityExpression NEXT
Binding it all together
Now we are ready to bind everything together.
Binding the AAA vServer to the Load Balancing vServer
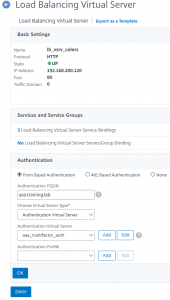
set lb vserver lb_vsrv_colors -AuthenticationHost aaa.training.lab -Authentication ON -authn401 OFF -authnVsName aaa_multifactor_auth
Binding policies to our AAA vServer
So we open our AAA vServer and select Advanced Authentication Policies
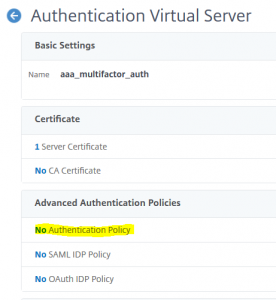 Click at No Authentication Policy
Click at No Authentication Policy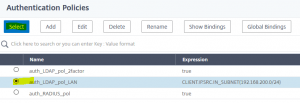 We select the “special case”, so the internal Lan Policy (aaa_LDAP_pol_LAN) first
We select the “special case”, so the internal Lan Policy (aaa_LDAP_pol_LAN) first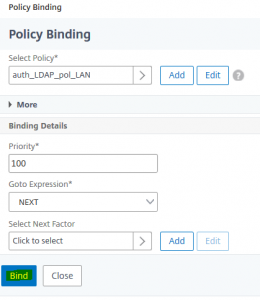 We bind it with a priority of 100 (that’s the default)
We bind it with a priority of 100 (that’s the default)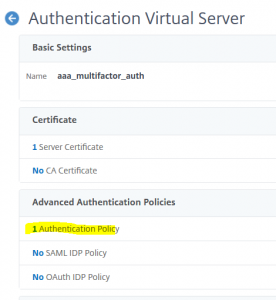 We click at 1 Authentication Policy, to bind the 2nd policy for “all the rest”
We click at 1 Authentication Policy, to bind the 2nd policy for “all the rest”
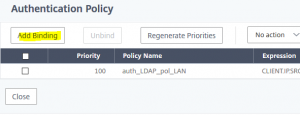 We click Add Binding
We click Add Binding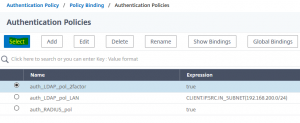 Select the default authentication Policy (aaa_LDAP_pol_2factor)
Select the default authentication Policy (aaa_LDAP_pol_2factor)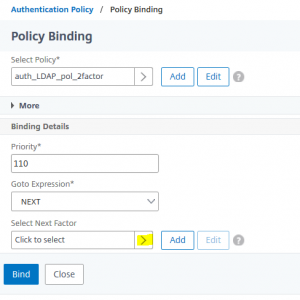 Bind it with a priority higher than before. Default is 110. Click Select Next Factor, to define, what to do after successfully authentication the 1st factor
Bind it with a priority higher than before. Default is 110. Click Select Next Factor, to define, what to do after successfully authentication the 1st factor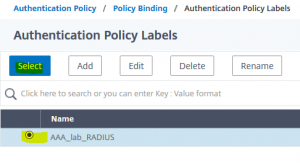 Select the RADIUS Policy (AAA_lab_RADIUS)
Select the RADIUS Policy (AAA_lab_RADIUS)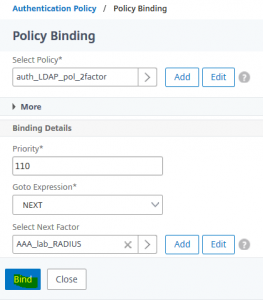 bind this policy
bind this policy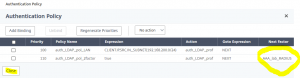 That’s what it should look like by now!
That’s what it should look like by now!
from command line:
bind authentication vserver aaa_multifactor_auth -policy auth_LDAP_pol_LAN -priority 100 -gotoPriorityExpression NEXT
bind authentication vserver aaa_multifactor_auth -policy auth_LDAP_pol_2factor -priority 110 -nextFactor AAA_lab_RADIUS -gotoPriorityExpression NEXT
The outcome
If you log on from 192.168.200.0 network, it will look like that:
Logging on from internal network
If you log on from 192.168.200.0/24 network, you will see a logon screen like that:
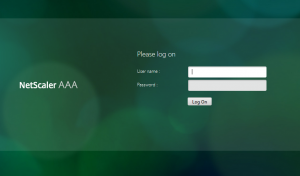 Logon will get processed by the 1st policy (auth_LDAP_pol_LAN), as the policy condition (CLIENT.IP.SRC.IN_SUBNET(192.168.200.0/24)) met (my client is 192.168.200.250)
Logon will get processed by the 1st policy (auth_LDAP_pol_LAN), as the policy condition (CLIENT.IP.SRC.IN_SUBNET(192.168.200.0/24)) met (my client is 192.168.200.250)
immediately after providing credentials you’ll get directed to the application
If you try to log on from outside (so any network other than 192.168.200.0/24), you’ll see the same logon screen as 1st factor:
Logon won’t get processed by the 1st policy (auth_LDAP_pol_LAN), as the policy condition (CLIENT.IP.SRC.IN_SUBNET(192.168.200.0/24)) is not met, but by the general one (auth_LDAP_pol_2factor). This one will invoke a 2nd factor. Therefore, immediately after lgging on, you’ll see an other logon screen, prompting for a RSA token:
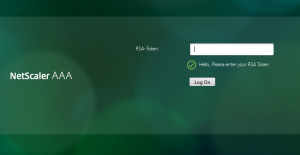 The application will only get visible after successfully logging on to this 2nd, additional, factor.
The application will only get visible after successfully logging on to this 2nd, additional, factor.
This is called cascading multifactor. Any policy you bind may invoke an other factor.
I hope you find this blog useful. I’d be glad to see your remarks
Johannes

Nice Article. i applied on my settings. My req is Smart card casscade to LDap. here is my setting
Certificate info:
1. Root 1 > Intermediate > Root 2 > Vdi.something.com (gateway vserver cert)
2. Root 1 > Intermediate > Root 2 > MySmartCardcert
3. Root CA 1 > MyLaptopCert
Vserver info:
1 IP address, 1 Cert, NO CA cert, 2 adv auth policy (config shown below), 1 schema login, 1default theme
Authentication setting
1Factor: Adv auth Pol > CERT Pol (100, true) > CERT Profile (Dual factor OFF, SAN-UPN) > NEXT
2Factor: Adv auth Pol > LDAP Pol (110, true) > LDAp Profile > Next > LDap Pol label > Ldap schema Pol > Schema Profile.
as i hit my portal, i was promt to select certificate and prompt to enter PIN (i guess 1st factor complete). then i was promt to select certificate again upon clicking OK. I recieved “cant reach this page securely”.. (2factor failed). What am i missing.
Thank you for your response.
Tuong, that’s a bit hard to say.
I agree, your 1st factor passed correctly. You should see hits for the policy. But as far as I see, you got the certificate-based logon bound twice, so there has to be a mistake in your bindings.
Probably, you could do some logging following this post https://norz.at/?p=572 (scroll a little bit down) to find out, which policies are hit and when.
Thanks a lot for the Articel. This worked very good for our OWA Load Balancing.
Now we switched from RADIUS to Citrix ADC Native OTP. Is something like this still possible?
Sure, should not be a problem. Just replace RADIUS with Native OTP