© image: Wikipedia
Two and a half years ago, I have written an article about LDAP. I always planned to add an article about RADIUS as well, but I never did. Today, I had to troubleshoot a RADIUS problem, so I did the necessary traces. It is a DUO server, but most other servers behave similarly.
Here we go!
What is RADIUS
RADIUS (Remote Authentication Dial-In User Service) is a protocol to authenticate users. Its last definition can be found in RFC 2865 (June 2000).
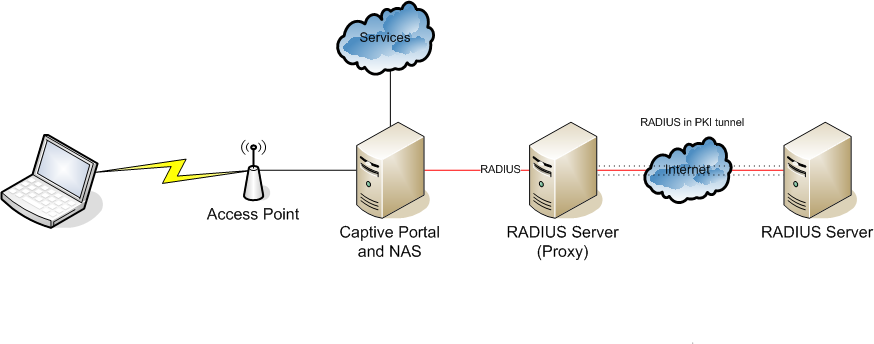
RADIUS is supported on Citrix ADC / NetScaler, both, for user-login to AAA and gateway vServers, and for administrator-login to the Citrix ADC / NetScaler itself. It is way simpler than LDAP and able to do accounting as well. Logon and accounting usually use different ports. Defaults are UDP 1812 for login and 1813 for accounting, but many RADIUS servers (RADIUS proxies) use non-standard ports.
Accounting is used to log logon/logoff events, so an administrator knows how long a user had been using the system (and probably charge it per minute). Accounting is not the focus of this article.
What does it take to log on through RADIUS?
A RADIUS policy is way simpler than an LDAP policy would be.
A RADIUS profile
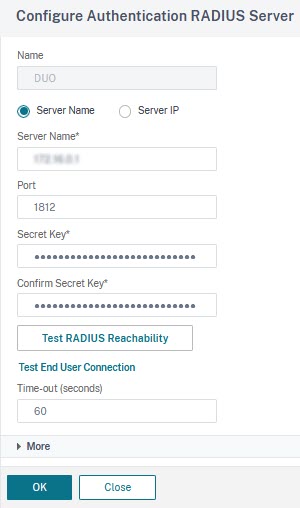
In general, it would be an IP address or the name of a server, a port, and a secret key. RADIUS works with pre-shared keys. Logons will fail if the key on the RADIUS authentication server and on NetScaler doesn’t match. The last parameter, the time-out, defaults to three seconds, however, RADIUS nowadays is usually sending challenges and waits for responses (SMS or push-messages, …), so it may need to get expanded to something like a minute, so users have a fair chance to respond. In my case, it is DUO, and users will have to commit to a challenge sent to the mobile phone. I give them a minute of time to locate and grasp the phone, unlock it and reply to the challenge. The authentication request will fail if a user takes longer to respond.
There would also be extended attributes like group membership, NAS-ID, password-encoding algorithm, and whether or not to do accounting. This must be defined by the manufacturer of the RADIUS server, but is usually left blank.
A RADIUS policy
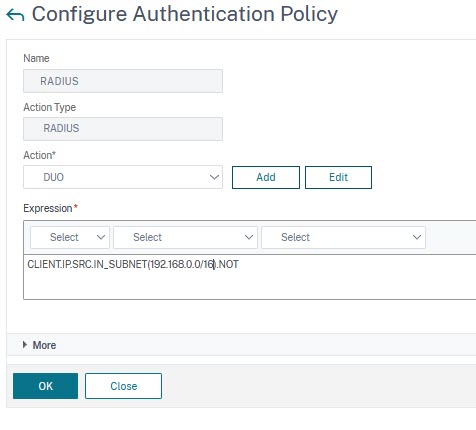
The RADIUS policy expression may be a simple true value (ns_true with classic policies), or limit access to certain IP subnets (as my screenshot shows)
The network side …
The main goal of this blog post is showing, what a RADIUS logon would look like from the network side.

The first thing catching our attention is the duplicated packets. That’s specific to this implementation (but rather common). RADIUS is using UDP, so there is no guaranteed packet delivery. In case one of these packets gets lost, there is still another one left. These packets are identical, so there are just two messages to get into: The RADIUS access request and the RADIUS access accept and reject.
The “RADIUS access request” message
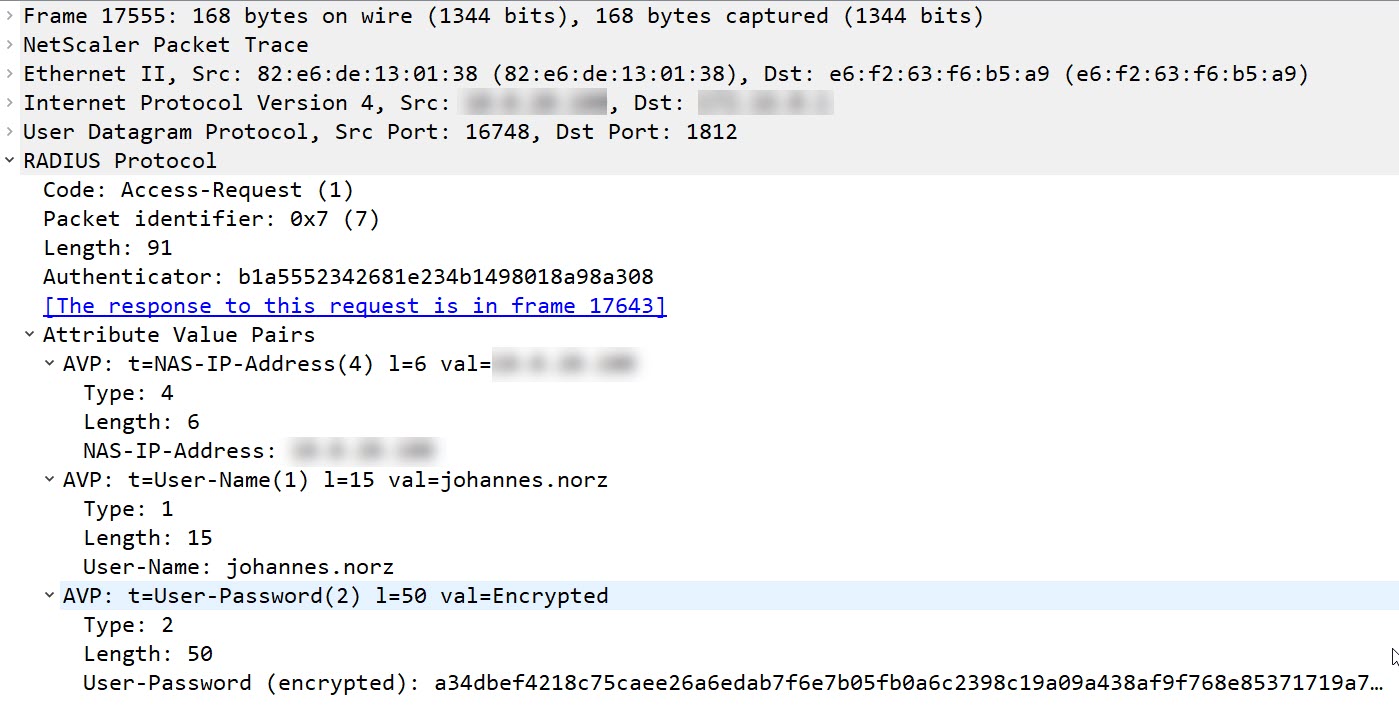
This UDP packet contains some value pairs, most important of all: The user-name, the NAS-IP address, and the password. All of them have a length parameter. Length is always 2 bytes more than the actual length.
- The NAS-IP-Address is used to identify the requesting system. This is done, using an IP address, as IP addresses are unique. The IP address used in the case of Citrix ADC / NetScaler is the NSIP. The length of an IP address is always 6 bytes, as an IP address always is a 4 bytes number.
- The User-Name is the name entered into the user name field. It is transmitted in plain text.
- The User-Password is encrypted and can’t be viewed easily.
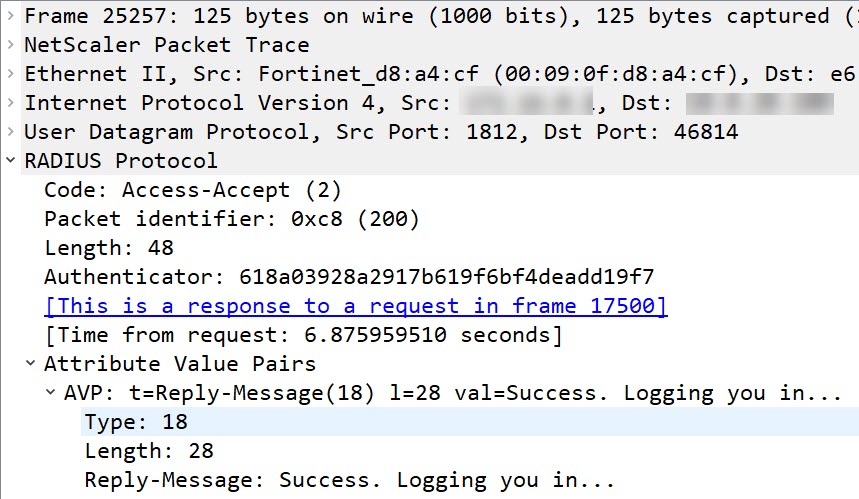
The “RADIUS access accept” message
This is a simple one: The type of message is success, the content might be different from vendor to vendor, in the case of DUO it’s the string “Success. Logging you in …”
The “RADIUS access reject” message
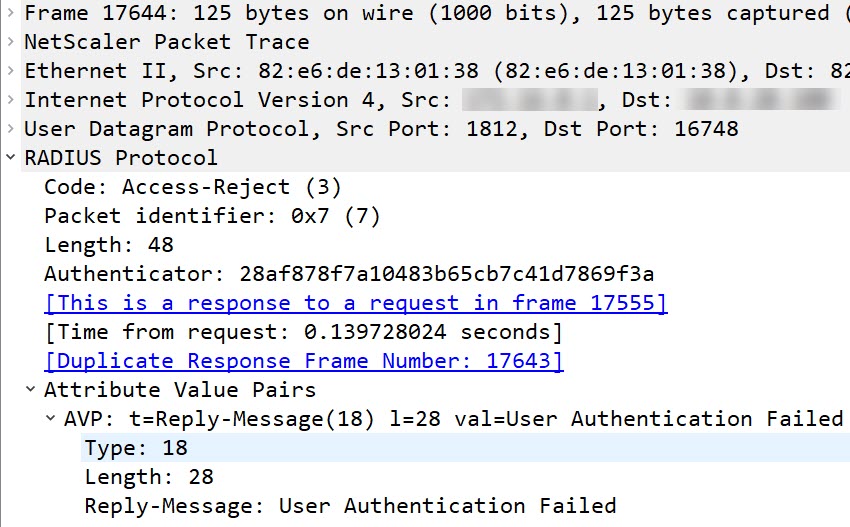
Similar to the “accept message”, however, with sad content.
Like always, I would be glad to hear your concerns, corrections, and what you miss in this article. Just drop me a comment!