As soon as our NetScaler Gateway is up and running we need to set up StoreFront to use it. It’s more a kind of introducing the NetScaler Gateway to StoreFront. Other than WebInterface StoreFront is designed to use a NetScaler Gateway, so it’s a rather easy thing to do.
Enabling Pass-Through authentication from NetScaler Gateway
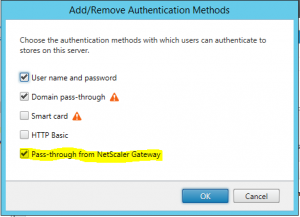
We open up StoreFront management console and click Authentication and select Add/Remove Methods on the right side.
We need to enable Pass-Through from NetScaler Gateway authentication. We can’t continue if we don’t!
Adding a NetScaler
Next step will be introducing our NetScaler to StoreFront, so it may be used by stores for remote access.
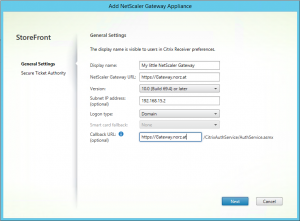
In StoreFront management console and click NetScaler Gateway and select Add NetScaler Gateway Appliance on the right side. A wizard opens.
- The name of our NetScaler Gateway is used in StoreFront only. You may choose the name you like best. Keep away from too funny or offending names, your boss may eventually see it 😉
- We add the FQDN of our NetScaler Gateway (it’s important to use the FQDN, exactly the same spelling as used on our certificate, or our HDX session will fail to launch!)
- The Subnet IP (SNIP) of your NetScaler Gateway. This is optional. You should not turn it on (following this post)
- Logon type is usually Domain. We have strong authentication on NetScaler Gateway, so we don’t need 2 factor authentication on StoreFront. Domain credentials get passed from NetScaler Gateway to StoreFront, so users won’t have to add their credentials twice.
- The Callback URL is an other optional parameter: the FQDN of the NetScaler Gateway. Again no point in skipping it. StoreFront contacts the NetScaler Gateway authentication service to verify that requests received from NetScaler Gateway. It’s mandatory if you use endpoint analysis scans on your Gateway and want to utilize these results in XenApp / XenDesktop to filter policies (“Citrix Smart Access”), as scann results are fetched from NetScaler Gateway during call back. It’s also used for session reliability.
It may be difficult to connect from StoreFront to NetScaler Gateway. There is a Citrix White paper about it. It’s quite old but still valid.
Click Next
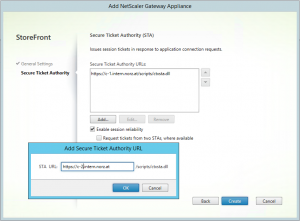
On next screen we have to set up STAs. The STA is a service inside the XML broker service and used to store the IP addresses of servers that will host the user’s session. It’s mandatory to have STAs for ICA proxy.
The XML broker service is located on every XenDesktop controller and every XenApp server for XenApp versions up to 6.5, so it’s nothing we have to install.
We have to use the same STAs in NetScaler Gateway, or we will run into trouble during the connection phase.
- We have to add STA servers. Citrix tends to encrypt all traffic using SSL, that’s why they suggest using SSL. In my opinion there is no serious content flowing too and from STA (just user name, application launched, the IP of the server responsible for this application too and a 32 byte random number, the STA ticket, back), so we don’t necessarily need to use SSL here.
Of course we should use two STAs as one of them may become unavailable and the other one will take over.
We should not load balance STAs (it would be possible here, but you must not do this on NetScaler Gateway or our sessions won’t launch!). So let’s just add two or more of our controllers here, they get load balanced by StoreFront servers. I always add the most preferred data collector here and one or more of the preferred ones in XenApp 6.5 or previous versions. - If we want to use session reliability we need to check this check box. Doing so will cause our STA tickets to remain inside the STA as long as our session lasts. Our client will be able to reconnect because of this.
- Using two STAs at the same time will avoid reconnection issues if the original STA server is currently down during reconnection attempts. It’s not mandatory, however may be a benefit and is of hardly any costs (STA tables get longer, so it’s a bit of waist of RAM on controllers, we are talking about MBs, no GBs).
Click Create to finish.
Enabling remote access
Our Storefront server now knows about our NetScaler Gateway. We just have to allow our store to use it. An easy one to do:
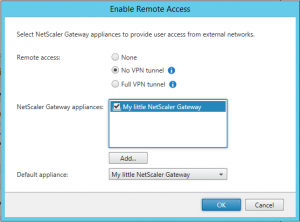
In StoreFront management console and click Stores, highlight one of your stores (or your store if there is just one) and select Enable Remote Access on the right side. A wizard opens.
- Remote access should not use a Full VPN tunnel (this would not be HDX proxy mode or so called “micro VPN” but full VPN access!) but No VPN tunnel. If you want to use a full VPN you don’t have to do anything within StoreFront as this is local LAN access as soon as you are connected to your VPN. However you would have to roll out VPN clients and VPNs are considered to be less secure than HDX proxy.
- Select your NetScaler Gateway.
Click Okay to finish.
Managing beacons
A beacon is an intentionally conspicuous device designed to attract attention to a specific location (Wikipedia).
We use our beacons to decide if our client is inside our LAN or on the internet. This will allow mobile clients to roam from extern to intern and vice versa without the need of reconfiguration. It only works with Citrix Receiver, it won’t work if you use a browser.
Citrix receiver will immediately try to connect to internal and external beacons if it gets started.
- If our client is inside of our LAN (so it can connect to the internal beacon, we don’t care about external ones) we will skip the NetScaler Gateway and directly connect to StoreFront. We will use one of StoreFront’s authentication methods (instead of NetScaler authentication) such as one factor domain authentication or domain pass-through authentication. Our Citrix Receiver will directly connect to the designated remote session host or virtual desktop.
- If the client is on the internet (so it can not connect to the internal, but to at least one of our external beacons) we will connect to NetScaler Gateway.
- If none of the beacons may get reached our client won’t try to connect and the user will see an error message if he tries to launch an application.
- Internal beacon: It defaults to Use the service URL. This is the base URL displayed (and managed) in StoreFront management console (click Server Group to see it).
The receiver will just do a HTTP (HTTPS) connection there (it will send a HEAD / command). You will have to change it if there is a HTTP service available on the internet for this URL. Specify a different beacon address in case. - There is no guide line for Extrenal beacons. They default to your NetScaler Gateway and https://www.citrix.com. You may use which ever web servers you like. Select highly available ones!

[…] setting up StoreFront 3 for NetScaler Gateway 11 […]