last update February 7th 2017
There are never versions about SSL-settings
We have previously created a NetScaler Gateway on our NetScaler 11. That’s great! Time to check if it’s secure. I usually use SSL labs SSL test, a widely used tool to test the security of a website.
I have an other blog about NetScaler virtual servers (contentswitching and loadbalancing SSL offloading servers). There is much more theory about SSL in that one. They do basically the same. This one may be great if you are interested in a bit more theory.
Let’s give it a try:
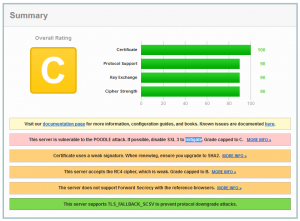
I agree, this is a disastrous result! Just a C- rating? C means: an insecure appliance, there are well known attacks that may compromise this appliance’s security!
Is a NetScaler a piece of shit?
Of course it’s not! However this wizard sets compatibility over security. Compatibility to old versions of Java, that’s why. So we’ll have to fix it!
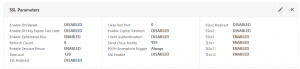
First issue clearly has to be the POODLE issue as it degraded our rating to C! This one is an easy one: just simply disable SSL V3. Go to NetScaler Gateway -> Virtual servers, open up your gateway, and check SSL parameters:
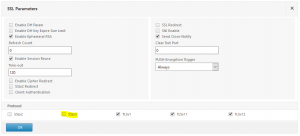
You see: SSL v.3 is enabled, and SSL v.3 is not considered to be secure. Just simply disable it: click on the pen i the top left corner of this section and uncheck SSL V.3
a new check with SSL labs is by far better:
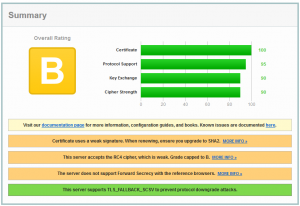
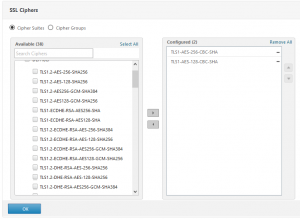
B means good. There are no well known attacks that could harm our NetScaler. Good is not good enough. What’s wrong now? “The server accepts RC4 cyphers”. RC4 is no more considered to be secure. I suggest removing all RC4 based cyphers from the list of supported cyphers. I removed all cyphers but the best we could use so far:
Make sure there are no other cyphers. Keep away from “Export” cyphers as these cyphers are really bad, keep away from RC4 cyphers. Also keep away from GCM cyphers as long as you did not upgrade to latest versions (11.1 Build 51.21,11.0 Build 69.12/69.123 or 10.5 Build 65.11). There is a big problem about GCM cyphers (see CTX220329 or here). Give it an other try:
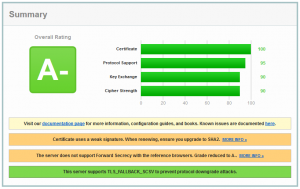
Ah! A-. A is very good. A- is still very good, however there may be some minor issues. I have two issues: First my certificate is a SHA1 certificate (and will get updated to SHA2 shortly), and 2nd I don’t support Forward Secrecy. I have already written a blog about this issue, so I don’t go into this. There is also a good one by Citrix how to get the highest rating, an A+ (outstanding security).
My 2 ciphers are not supported by Windows XP! This may turn out to be an issue! SSL Labs will list issues like that. I can go with it, so I don’t care about it.
Our NetScaler Gateway can now be considered to be secure.
Attention!
I’d suggest checking security of your gateway on a regular base. Your NetScaler may drop down to D (there is an actual security thread affecting this site) or even worse if new issues arise. I’ll keep an eye on it and will continue reporting how to fix issues!
Next thing might be enabling NetScaler Gateway HDX Proxy mode (formally known as ICA Proxy mode)

[…] Making it a bit more secure […]
Have you thought about doing this one from the same web site creators?
https://securityheaders.io
The netscaler gets a D grade. Im not smart enough on how to fix the issues.
This scan is not about SSL, so it’s a different peace of cake, it’s done by a completely different team and targets completely different threats. Because of this it’s possible to score an A+ with SSL and fail their test completely. The issues (my issues) are about “missing” HTTP headers. I didn’t know this scann, so I’ll have to go into it. On first sight: they check for headers I didn’t to put in. Maybe I will write something about it. Basically you would have to create a bunch of rewriting policies adding headers into your responses and bind them globally.
[…] on an excellent blog by Steven Wright in Citrix Blogs. I have an other blog about scoring an A+ on NetScaler Gateway (Unified Gateway). The other one is a bit less informative […]
[…] Similar but newer posts: Changing my Citrix NetScaler VPX based website from http to https and scoring an A+ in SSL labs test and Making a NetScaler Gateway on NetScaler 11 a bit more secure […]