last update: February 7th 2017
Similar but newer posts: Changing my Citrix NetScaler VPX based website from http to https and scoring an A+ in SSL labs test and Making a NetScaler Gateway on NetScaler 11 a bit more secure
ECDHE Ciphers, this means, Elliptic curve Diffie–Hellman type of cyphers, add additional security to a NetScaler. If we want to use this kind of cyphers we need to create a DH key and enable curves.
Creating the key (optional, not needed if you want to go with ECDHE cyphers)
I thought this is a mandatory step, however it’s not. We don’t need to create and bind a DH key. Stefan Wendrich corrected me about that.
The first thing to do is creating the key. This can be done from trafic management -> SSL
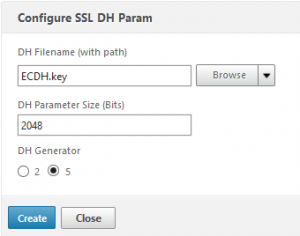
give your key a name. DH paraeter size may be 512, 1024 or 2048. The smaller the key size, the less burden for your NetScaler, the larger it is the more secure. I tend to go with 2048. I have no preference for DH generator parameters. It takes some wile to create this key!
Enabling DH with a vServer
Diffie Hellmanhas to be enabled on a vServer.
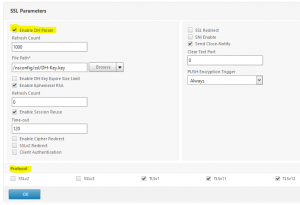
Most important: Select Protocols. If you don’t need to support legacy OS like Internetexplorer on Windows ‘9x you should disable SSL V3. Most modern OS support TLS 1.2, however some don’t, so you may want to leave TLS v1 and 1.1 enabled, enable the most current one, TLS 1.2!
Enable DH. You may set up a refresh count, 0 means no refresh. Refreshing means recreating a DH key pair. Refresh is a burden for your NetScaler (especially for a VPX!), so don’t set this parameter too small; leave it to 0 if you’re concerned about CPU waste and give a sh** on security!
Select your DH key created before by browsing for it. They should be located in /nsconfig/ssl.
Enable DH Key Expire Size Limit. This will set the private key size to a proper value
Enabling curves
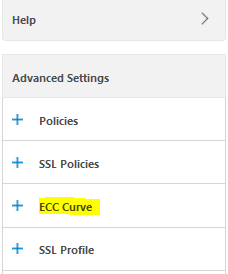
There is a set of 4 curves available with ECDH:
- P_256
- P_384
- P_224 (not supported with TLS 1.2 on MPX)
- P_521 (not supported with TLS 1.2 on MPX)
None of them is enabled (this depends on NetScaler version). Click the + sign at the right side and enable curves. I usually enable all curves.
Selecting SSL cyphers for a vServer
Last not east you’ll have to select cyphers. The cyphers I selected are:
- TLS1-ECDHE-RSA-AES256-SHA
- TLS1.2-ECDHE-RSA-AES-256-SHA384
- TLS1.2-ECDHE-RSA-AES256-GCM-SHA384 No more considered to be secure see CTX220329
- TLS1-AES-256-CBC-SHA
TLS1-AES-256-CBC-SHA is for backward compatibility only: it will be used if some client does not support ECDHE. This cypher suite does not support forward secrecy.

[…] my certificate is a SHA1 certificate, and 2nd I don’t support Forward Secrecy. I have already written a blog about this issue, so I don’t go into this. There is also a good one by Citrix how to get the highest […]
[…] is a blog about this. I have written it about NetScaler Gateway, but it’s also valide for a load balancing or a […]
Hi,
nice article. But for only ECDHE ciphers, you dont need a Diffie Hellmann key. For ECDHE you need only the ECC curves.
See this blog post from citrix https://www.citrix.com/blogs/2016/06/09/scoring-an-a-at-ssllabs-com-with-citrix-netscaler-2016-update/
At the end about ECDHE FAQ:
###
The DHE ciphers in the custom cipher group above will remain disabled if you don’t bind a DH key. ECDHE doesn’t require one.
###
Thanks! Great point, I’ll go into this soon!
You’re absolutely right. Just gave it a try …
thank you for sharing
Can ECDHE work with other applications?
ECDHE is just a standard for SSL syphers. So sure, if the client device supports TLS 1.0.