It is quite easy to set up a NetScaler Gateway on NetScaler 11. It’s quite similar to NetScaler 10.5, but the wizard is much more powerful now! I’ll show you how to do it.
Prerequisites
I assume you have:
- a certificate in place. This certificate should be a valid certificate created by a trusted certificate authority. If you don’t know how to get or create a certificate: there is an entry about this subject in my old blog
- a LDAP and optionally a RADIUS policy to log on.
- an IP address to be used for NetScaler Gateway inside your DMZ. This IP won’t be visible from outside, your fire wall will point an external IP to this internal one. This IP may be in use by an other load balancing vServer, however it must not be in use for SSL (or you may use a different port like 1443). I strongly recommend using a new IP for this!
Starting the NetScaler Gateway Wizard for XenApp and XenDesktop
We will start the brand new and shiny NetScaler Gateway Wizard. It’s located on the left side in the lower section.
Click Get Started
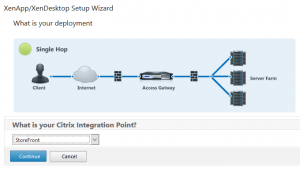
We select StoreFront. We could also select WebInterface, if we would still use WebInterface (we should not do this as WebInterface is outdated).
Click Continue
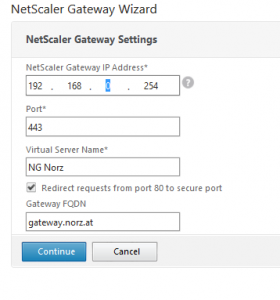
- Set an IP address for your NetScaler. This IP address will be the IP address of your NetScaler Gateway inside your DMZ.
- Same with the port. The port defaults to 443, and there is hardly any reason to change it.
- Select a name you like. Try to be not too funny, your boss will eventually see it some day 🙂
- If you want to allow users just to connect to this gateway and let NetScaler redirect them to HTTPS you check this “Redirect …” checkbox and provide the FQDN users will use. In this example it will forward from https://gateway.norz.at to https://gateway.norz.at. NetScaler Gateway Wizard will create a load balancing vServer to do this. This server appears to be down. This is by design and is no issue!
Click Continue
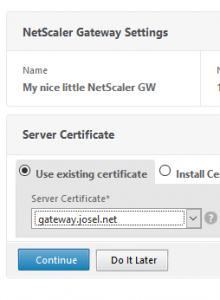
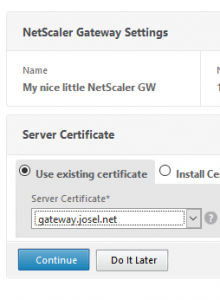
Select your certificate. You could alternatively add a certificate now as shown in the next screen shot, but I strongly suggest installing it prior to running this wizard!
Click Continue
click Continue
Select your certificate. You could alternatively add a certificate now as shown in the next screen shot, but I strongly suggest installing it prior to running this wizard!
click Continue
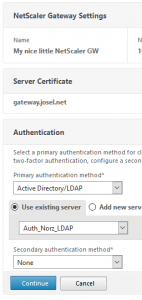
Next you’ll select the proper authentication method. In most cases this would be Microsoft Active Directory, a LDAP source from perspective of a NetScaler. You might also use a 2nd source for authentication (2 Factor authentication). In most cases this would be a RADIUS based authentication like RSA tokens or a SMS based method.
Be sure to put the 2nd Method (RADIUS) on top. Doing so will prevent hackers causing an account lockout in Active Directory, as the 2nd Method is not used if the 1st one fails!
click Continue
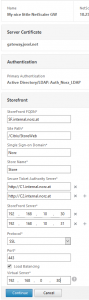
This is a rather big one: It will set up our connection to StoreFront. It will do not only this but also install load balancing for StoreFront servers.
- set the FQDN for your StoreFront service. This FQDN has to be resolvable from NetScaler.
- the site path to your web store. It’s usually /Citrix/<store-name>web. Look into your StoreFront console to see it’s URL.
- We authenticate to NetScaler Gateway using username and password only. However Active Directory needs to know the name of the domain desired. So we have to specify the name here.
- The store name. The default store name is Store. Look into your StoreFront console to see the name of the desired store.
- STAs: You may specify as many as you like. STAs store the internal IP address of the desired XenApp or XenDesktop resource, so it is not passed to the client but a so called STA ticked instead. You may ad as many as you like, but I’d suggest specifying at least two of them. You must not load balance STAs!
Citrix usually suggests to use HTTPS for STA traffic, but it’s not mandatory as there is no confidential data in STA traffic. - StoreFront Server’ IP addresses have to be specified here. This is to create load a balancing vServer for StoreFront
- The protocol in use may be HTTP or SSL (HTTPS). I strongly suggest using SSL as traffic to StoreFront contains user name and password in plain text!
- The port in use. It’s usually 80 for HTTP or 443 for SSL
- We may create a load balancing vServer for our StoreFront servers specified above. If you want this wizard to do so check the check box
- The IP address for the load balancing vServer created to load balance our StoreFront servers
Click Continue
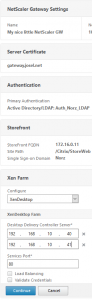
Last not least, let’s specify our XenDesktop farm. We could also specify a XenApp farm for XenApp versions up to 6.5.
- The IP addresses of our XenApp servers
- the port for the XML service (usually it’s port 80)
- if we want to create a load balancing vServer we could check this checkbox and specify an IP address to be used for this. I would not do this inside your DMZ, so I skipped this
Click Continue
Now our Gateway is finished!
still some more work to be done!

[…] have previously created a NetScaler Gateway on our NetScaler 11. That’s great! Time to check if it’s secure. I usually use SSL labs […]
[…] have previously set up our NetScaler Gateway and made it more secure. Now it’s time to configure it for HDX Proxy mode (formerly known as […]
if you cant spell “Method”, how do you expect anyone to take this article seriously, you have lost all credibility
Oh, thanks. Let’s hope writing method in German instead of English is the worst error in my blog! I very much like your positive feedback. I corrected this mistake. I guess everything is perfect and my credibility is fine now 😉
Hi Johannes, hope you’re well. I was on the early access Netscaler 11 course you ran in Dublin in Nov 2015 (as a virtual delegate). Just wondering if you (as an “insider”) have any idea when Citrix might release v11 Netscaler exams? I can’t get anything out of Citrix training. I’d rather not sit the 10.5 exams if they’re about to release v11. By the way ….. on the course your English was way better than my German, so no complaints from me! Cheers Nick
Hi Johannes, I have the same query as Nick said above, when Citrix might release v11 Netscaler exams? I’ll rather wait for ver.11 instead of sitting for 10.5 exam. Thanks in advance.
Sorry for not answering. Currently Citrix is going to update CNS 301 class to version 11; however the safe harbour build is still a 10.5 (61.11). The test will follow the safe harbour built (follow, not accompany! There might be a gap of some weeks to month). So there is no stress for Citrix.
I guess updates to tests will be updated some time in spring. Keep in mind: there is currently no official announcement of an update being on the way!
Your article helped a lot! Thanks much!
Great! Thanks for telling me!
“Same with the port. The port defaults to 443, and there is hardly any reason to change it.”
If I want to change it: what might be the consequences? Of course I have to change it in Storefront too…
The consequence of using 12345 as a port would be: Many people would not be able to connect, as their client side firewall would block access to this port. Unfortunately you won’t be able to influence client side firewalls in many cases as they are owned by 3rd parties (hotels, companies, …). And of course your firewall needs to permit access …