Sometimes, we need specific attributes like an E-Mail address or the userPrincipalName to be passed from a SAML IDP to the SP. If you use a Citrix ADC / NetScaler as SAML IDP, it is, indeed, an easy thing to do. Let’s have a look.
Extracting attributes from LDAP
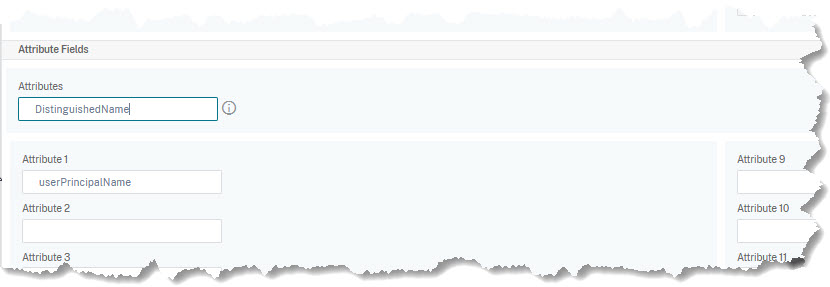
The first step, of course, is always to retrieve an attribute from LDAP. This is done via an LDAP policy. I won’t go into LDAP policies in general. If you scroll down to the end, you’ll see a link to show more settings. Click it, and scroll down even further.
 Setting the attribute via command-line:
Setting the attribute via command-line:
set ldapaction act_ldap -attribute1 userPrizipalName
There is a maximum of 17 attributes you can extract from LDAP.
Passing Attributes via SAML
The next step would be, passing these attributes to the SAML IDP via SAML assertions. Again, I assume, you know how to set up a Citriox ADC / NetScaler as a SAML IDP (if not, see here). It’s just about passing attributes.
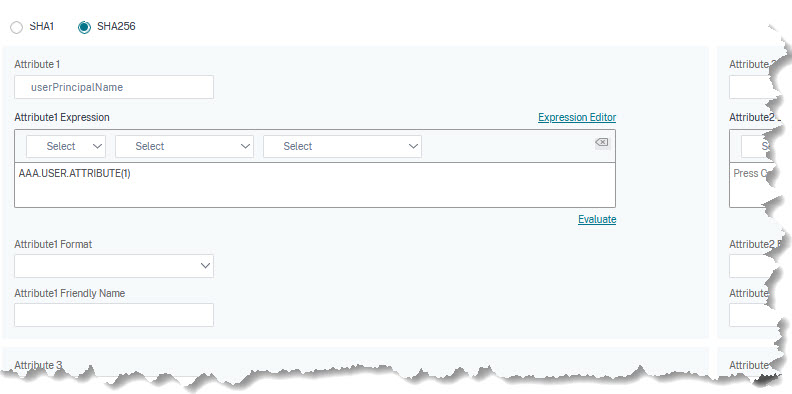
Open the SAML IDP action. Scroll down to the end and click more. You find attributes at the end of the page. In this example, I pass the userPrincipalName attribute:
Setting the attribute via command-line:
set samlidPProfile SAML_IDP_profile -Attribute1 userPrincipalName -Attribute1Expr "AAA.USER.ATTRIBUTE(1)"
AAA.USER.ATTRIBUTE is an array, containing all attributes extracted by the authentication action. LDAP-Attribute1 is is ATTRIBUTE(1), LDAP-Attribute2 is is ATTRIBUTE(2) and so on.
Passing the password
First things first: Passing the password from SAML IDP to SAML SP does not make sense from a security perspective. However, it’s possible and not hard to do. Just pass AAA.USER.PASSWD:
set samlidPProfile SAML_IDP_profile -Attribute2 Password -Attribute2Expr "AAA.USER.PASSWD"
Be careful: Passwords sent may be incomplete! You have to encode special characters!
