last update: October 2nd 2018
This is the second part of debugging logon. The first one, a network trace about LDAP, may be found here.
Citrix ADC / NetScaler logs all events related to AAA (authentication, authorization, auditing) to /tmp/aaad.debug
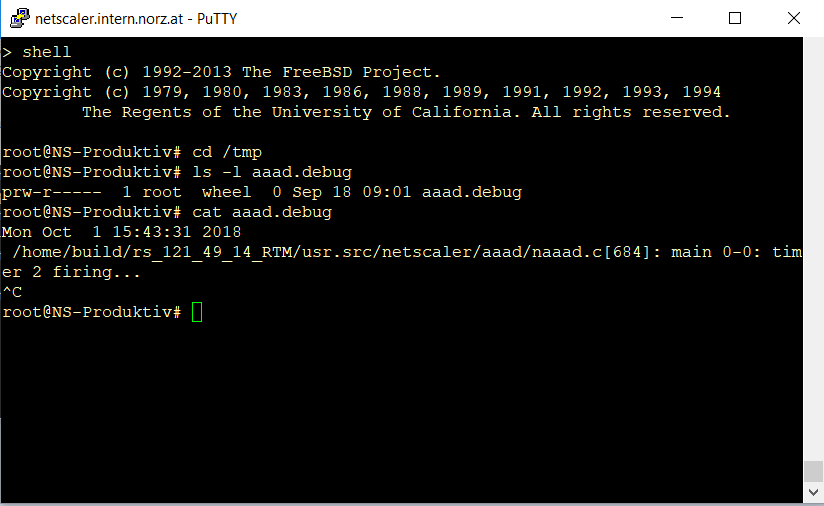
You need to be nsroot or superuser to successfully log on to the BSD shell. This is a requirement to change to BSD shell. Change to the /tmp directory. There you find a file called aaad.debug. A file? No, it’s a pointer. Pointers always have a size of 0 and point to the output of a process, in this case to the aaa-deamon.
Doing analysis on a real world aaad.debug output
To examine the logon process, you will have to start debugging.
cat aaad.debug
Press [ctrl]+C fter finnishing your logon-attempt.
It was done on firmware version 12.1.49.23. I have not removed any lines, but I don’t explain all of them as they are many and some are of no importance to me.
There are several phases:
- Initialization phase
- Picking the first policy
- Initiating comunication to first server
- Logging on the Administrative Bind DN
- Looking up the user
- Checking user’s password
Mon Oct 1 15:24:31 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[684]: main 0-0: timer 2 firing…
This is a periodic message. It is on no importance to our debugging and may safely be ignored.
Initiating authentication
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[886]: process_kernel_socket 0-14029: partition id is 0Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[1093]: process_kernel_socket 0-14029: ns_aaad_decrypt_auth not done
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[1127]: process_kernel_socket 0-14029: call to authenticate user :johannes.norz, vsid :10315, userlen 13
This is the beginning of the actual logon process
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[1176]: process_kernel_socket 0-14029: call to authenticate user:johannes.norz, vsid :10315, req_flags 2
Yes! That’s what we want! Let’s authenticate this johannes.norz!
Communicating to an authentication source
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[4685]: start_cascade_auth 0-14029: starting cascade authentication
Authentication in Citrix ADC / NetScaler is a so called cascading authentication. This means, we start with the most important authentication policy (the one with the lowest binding priorty) and walk them all down to the last one.
We authenticate to the first policy. If we are able to authenticate successfully we stop here. If we fail, no matter why (user not found, invalid password) we’ll try the next one and so on.
Initiating comunication with the first policy
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[4795]: cascade_auth 0-14029: starting ldap auth for: johannes.norz, sizeof(*ar) is 28, userlen 14
My first policy is a LDAP policy, so we do LDAP. The length of the username is 13 characters plus a trailing character 0, so 14 characters passed to this policy.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[117]: start_ldap_auth 0-14029: Starting LDAP auth
Authentication started using this LDAP policy
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[141]: start_ldap_auth 0-14029: attempting to do ldap auth for johannes.norz @ 192.168.0.15
So we try to authenticate this johannes.norz to LDAP server at 192.168.0.15
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[143]: start_ldap_auth 0-14029: LDAP referrals are OFF
Referrals this is about cross domain logon. It’s a Microsoft topic. We don’t search across domains, so it’s turned off by default.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[144]: start_ldap_auth 0-14029: LDAP referral nesting depth 0
This is about searching foraing domains. As referrals is turned off we searf 0 additional domains.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[843]: continue_ldap_init 0-14029: Connecting to:192.168.0.15:389
Finally we connect to 192.168.0.15 on LDAP standard TCP port 389.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[5013]: register_timer 0-14029: setting timer 56004
setting a time-out for this authentication attempt.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[5090]: unregister_timer 0-14029: releasing timer 56004
clearing that timer.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[923]: ns_ldap_set_up_socket 0-14029: Server certificate hostname = NULL
This is plain text LDAP. Plain text LDAP is a security risk, so you should change to TLS or SSL instead! Passwords get transmitted unencrypted in plain text LDAP. See my post about LDAP authentication network traces!
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[970]: ns_ldap_set_up_socket 0-14029: Set cert verify level 0
We would not verify the issuer of a certificate presented by this LDAP server. This is a global SSL setting (Load balancing → SSL: Change advanced SSL settings → Strict CA checks)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[973]: ns_ldap_set_up_socket 0-14029: Getting cipher suite global value
Not needed here as this is plain text. It’s about ciphers. Only valid with TLS / SSL. I skip some more SSL related settings as I’m not interested in these.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[976]: ns_ldap_set_up_socket 0-14029: Checking non-zero cipher suite
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[986]: ns_ldap_set_up_socket 0-14029: NULL cipher suite. Using default.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[992]: ns_ldap_set_up_socket 0-14029: Freeing cipher suite value
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[999]: ns_ldap_set_up_socket 0-14029: Done with cipher suite
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[1072]: ns_ldap_set_up_socket 0-14029: Sectype: 1
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[1077]: ns_ldap_set_up_socket 0-14029: Successfully established connection to NULL
I love this one: We successfully connected to the LDAP server, so all firewalls are OK, the server is up and running, a perfect result for the connection phase!
Logging on the Administrative Bind DN
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[5013]: register_timer 0-14029: setting timer 56005
so again: setting a timer for this logon attempt. Logon will fail if server is not fast enough.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[197]: receive_ldap_bind_event 0-14029: receive ldap bind event
So let’s start authenticating administrative bind DN!
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[439]: ns_ldap_check_result 0-14029: checking LDAP result. Expecting 97 (LDAP_RES_BIND)
Let’s check if this was successful?
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[477]: ns_ldap_check_result 0-14029: ldap_result found expected result LDAP_RES_BIND
That’s an other one I like: We made it (as expected)!
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[209]: receive_ldap_bind_event 0-14029: Bind OK
so bind attempt was OK (as we already know)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[5090]: unregister_timer 0-14029: releasing timer 56005
so we unset the timer
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[278]: receive_ldap_bind_event 0-14029: Original slen: 13
Looking up the user
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[302]: receive_ldap_bind_event 0-14029: User name: dirty = <johannes.norz> sanitized = <johannes.norz>
We start authentication from here: The user we want to authenticate is johannes.norz. “Dirty” as this is it’s user name, not the LDAP user name.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[304]: receive_ldap_bind_event 0-14029: Admin bind successful, attempting user search event for johannes.norz
So let’s search for this user’s LDAP user name.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[1843]: get_email_attribute 0-14029: Email attribute: <mail>, length 5
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[1238]: ns_ldap_search 0-14029: Searching for <<(| (objectClass=domainDNS) (& (sAMAccountName=johannes.norz) (objectClass=*)))>> from base <<dc=intern,dc=norz,dc=at>>
So we’re gona search for a user called johannes.norz in a LDAP directory called dc=intern,dc=norz,dc=at (AD name: intern.norz.at)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[5013]: register_timer 0-14029: setting timer 56006
Again, setting a timer. Attempt will time out if the domain controller is not fast enough.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[1262]: ns_ldap_search 0-14029: Sent user search query.
finally we asked the domain controller about this user. We’re waiting for a reply.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[399]: receive_ldap_user_search_event 0-14029: Received LDAP user search event.
And we received a reply!
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[439]: ns_ldap_check_result 0-14029: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Let’s see what we received?
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[443]: ns_ldap_check_result 0-14029: Got result 0. Non-event, continuing
100% honest: I don’t understand this one. Seems like we did not yet see useful results. This will go on for a while.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[399]: receive_ldap_user_search_event 0-14029: Received LDAP user search event.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[439]: ns_ldap_check_result 0-14029: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[443]: ns_ldap_check_result 0-14029: Got result 0. Non-event, continuing
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[399]: receive_ldap_user_search_event 0-14029: Received LDAP user search event.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[439]: ns_ldap_check_result 0-14029: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[443]: ns_ldap_check_result 0-14029: Got result 0. Non-event, continuing
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[399]: receive_ldap_user_search_event 0-14029: Received LDAP user search event.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[439]: ns_ldap_check_result 0-14029: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[443]: ns_ldap_check_result 0-14029: Got result 0. Non-event, continuing
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[399]: receive_ldap_user_search_event 0-14029: Received LDAP user search event.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[439]: ns_ldap_check_result 0-14029: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[443]: ns_ldap_check_result 0-14029: Got result 0. Non-event, continuing
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[399]: receive_ldap_user_search_event 0-14029: Received LDAP user search event.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[439]: ns_ldap_check_result 0-14029: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[477]: ns_ldap_check_result 0-14029: ldap_result found expected result LDAP_RES_SEARCH_RESULT
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[411]: receive_ldap_user_search_event 0-14029: received LDAP_OK
Mon Oct 1 15:24:33 2018
Finally: We found this very user! (so the user is there. It would return an error if this user is not a member of this LDAP. We still don’t know anything about the password!)
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[5090]: unregister_timer 0-14029: releasing timer 56006
we have set this timer, so we have to release it
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[441]: receive_ldap_user_search_event 0-14029: Binding user… 2 entries
OK. Perfect. So let’s do analysis
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[442]: receive_ldap_user_search_event 0-14029: Admin authentication(Bind) succeeded, now attempting to search the user johannes.norz
Is this the right record (it will always be as long as your AD is OK)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[445]: receive_ldap_user_search_event 0-14029: Number of entires in LDAP server response = 2
There are 2 entries in server response (this was expected)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[459]: receive_ldap_user_search_event 0-14029: [0]: Object = 0x29ea2580
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[657]: extract_ldap_multi_value_attribute 0-14029: While retrieving ldap attribute objectClass, 3 attribute values found for johannes.norz
This user has 3 attributes in it. So we extracted these atributes, I don’t understand the next some lines in detail, if you do, please tell me!
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[336]: check_for_domain_dns 0-14029: Extracted attribute, name: objectClass, value: top,domain,domainDNS
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[340]: check_for_domain_dns 0-14029: Found objectClass of type domainDNS
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[476]: receive_ldap_user_search_event 0-14029: Updated usrobj_domaindns for user johannes.norz
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[459]: receive_ldap_user_search_event 0-14029: [1]: Object = 0x29ea25c0
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[657]: extract_ldap_multi_value_attribute 0-14029: While retrieving ldap attribute objectClass, 4 attribute values found for johannes.norz
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[336]: check_for_domain_dns 0-14029: Extracted attribute, name: objectClass, value: top,person,organizationalPerson,user
This is a user object (culd be ay other object in AD like a computer, a group, …)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[344]: check_for_domain_dns 0-14029: Did not find objectClass of type domainDNS
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[485]: receive_ldap_user_search_event 0-14029: Updated usrobj for user johannes.norz
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[515]: receive_ldap_user_search_event 0-14029: User DN= <<CN=Johannes Norz,OU=Users,OU=Our’s,DC=intern,DC=norz,DC=at>>
This is what I wanted to see: The LDAP user name of this user! This line proves: This is a valid LDAP user, the user is there and we may continue logging on this user. Together with this user we also received some more attributes, so next we will look into these.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[2184]: check_pwd_last_set 0-14029: pwdLastSet = 181148089699403926, value = 43522
we may need some attributes in addition. For example: This password was set last May
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[2210]: check_max_pwd_age 0-14029: maxPwdAge = -863136000000000, value = 999
This is the mayimum age for passwords (this user is not mandated to change his password)
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[2247]: set_days_for_pwd_exp 0-14029: (set_days_for_pwd_exp) INPUT: pwd_last_set = 42622, max_pwd_age = 999
Again, values needed to force a password-change plus several more, I skip these.
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[2260]: set_days_for_pwd_exp 0-14029: days_since_1970 = 17806, days_since_pwd_last_set = 752, days_for_pwd_exp = 247
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[624]: extract_ldap_attribute 0-14029: retrieved pwdLastSet value 131178981698422956 for johannes.norz, length is 18
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[1843]: get_email_attribute 0-14029: Email attribute: <mail>, length 5
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[560]: extract_ldap_attribute 0-14029: While retrieving ldap attributes mail attribute not found for johannes.norz
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[1843]: get_email_attribute 0-14029: Email attribute: <mail>, length 5
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[710]: receive_ldap_user_search_event 0-14029: Failed to extract attribute, name: mail
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[1843]: get_email_attribute 0-14029: Email attribute: <mail>, length 5
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[730]: receive_ldap_user_search_event 0-14029: For user johannes.norz, group stringLength 21
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[739]: receive_ldap_user_search_event 0-14029: built group string for johannes.norz of:PublishedApps
FaNorz
This is about group membership: This user is member of 2 groups, PublishedApps and FaNorz. This is an important information as we use groups to grant access to applications and set session policies.
Checking user’s password
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[770]: receive_ldap_user_search_event 0-14029: User search succeeded, attempting user authentication(Bind) for <johannes.norz>
Now we know the name of this user, we try to authenticate it!
Mon Oct 1 15:24:33 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[5013]: register_timer 0-14029: setting timer 56007
Again, setting a timer. Authentication will fail if AD is too slow
Mon Oct 1 15:24:34 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[1450]: receive_ldap_user_bind_event 0-14029: Got user bind event.
We received data from AD
Mon Oct 1 15:24:34 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[439]: ns_ldap_check_result 0-14029: checking LDAP result. Expecting 97 (LDAP_RES_BIND)
Let’s see what it is?
Mon Oct 1 15:24:34 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_common.c[477]: ns_ldap_check_result 0-14029: ldap_result found expected result LDAP_RES_BIND
It’s a result we expected
Mon Oct 1 15:24:34 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[1459]: receive_ldap_user_bind_event 0-14029: Bind OK.
Heureca! It’s an OK! So the password specified was OK. Result could also have been a fail.
Mon Oct 1 15:24:34 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[5090]: unregister_timer 0-14029: releasing timer 56007
Let’s kill the timer, we already received a result.
Mon Oct 1 15:24:34 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/ldap_drv.c[1553]: receive_ldap_user_bind_event 0-14029: User authentication (Bind event) for user johannes.norz succeeded
We authenticated it successfully.
Mon Oct 1 15:24:34 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[3530]: send_accept 0-14029: sending accept to kernel for : johannes.norz
A message to kernel: johannes.norz is a kosher user! No problem about this guy!
Mon Oct 1 15:24:34 2018
/home/build/rs_121_49_14_RTM/usr.src/netscaler/aaad/naaad.c[3448]: aaad_alloc_serialize_keyValue_attrs 0-14029: Total attribute values to PE : 53, pwd_last_set=131178981698422956
Some more information about passwords.
Hope this one was useful to you. I’d be glad to get feedback or some more insight information on understanding this aaad.debug log. Just comment to this article!
