
There is one thing different about a Citrix ADC WAF (Web Application Firewall) compared to most other features in Citrix ADC: It will affect your whole ADC deployment as soon as you turn it on.
It you would, for example, turn on rewriting feature (enable feature RW), it would probably add a microsecond or two to packet processing, but apart from this not affect anything, as there are no policies bound. The Citrix ADC (NetScaler) WAF is different, as it got some default settings and has a default policy bound. It is one of the four built in profiles, named APPFW_BYPASS.
You may change the default profile by clicking to Security → Citrix Web App Firewall. In the right section click Settings → Change Engine setting.
There are some more things affected: Citrix NetScaler ADC WAF will strip some headers and might change the HTTP version. I will go into that, but first I’ll talk about engine settings and default profiles.
Engine settings
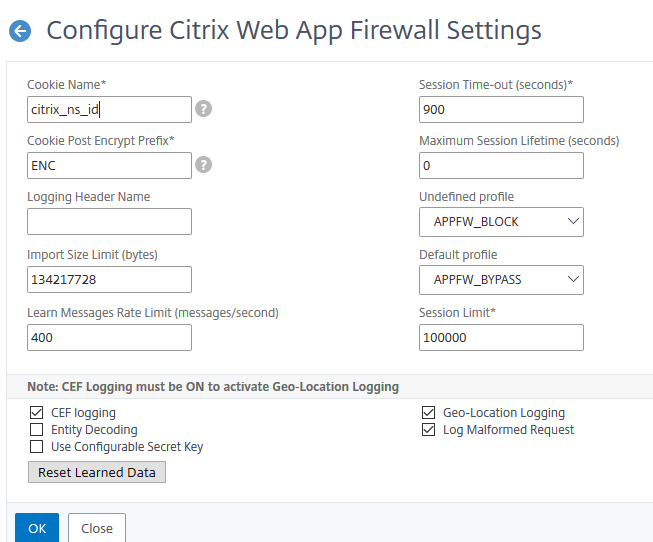
There are several default settings, applying to all HTTP servers immediately as soon as you enable the Feature. I will explain all of them.
Cookie Name*
The name for session cookies. It is important to set this name before enabling the cookie consistency check. This cookie is used to track sessions for several Citrix ADC WAF scans.
I would suggest changing this name as we don’t need to tell people about the WAF product we’re actually using. I don’t want to make life for bad guys that easy.
Cookie consistency check will add additional cookies: citrix_ns_id_wlf (will fife forever, used with persistent cookies) and citrix_ns_id_ wat (will act transient for session cookies). If you change the cookie name, these _wlf and _wat cookies change their names as well, but keep their extension.
Cookie Post Encrypt Prefix*
Used with cookie encryption, contained in consistency scan. This prefix gets added to cookies after encryption. Again, I’d suggest changing it as it’s a fingerprint for Citrix NetScaler ADC WAF. Make sure this prefix does not appear in non-encrypted cookies as NetScaler would probably try to decrypt these.
Used with cookie encryption, contained in consistency scan. This prefix gets added to cookies after encryption. Again, I’d suggest changing it as it’s a fingerprint for Citrix NetScaler ADC WAF.
Make sure this prefix does not appear in non-encrypted cookies as NetScaler would probably try to decrypt these. It could cause problems.
Logging Header Name
The name of the header holding the client’s IP. Citrix ADC WAF will log the IP address in IP packets if you don’t specify this header. It’s used if there is a proxy device in front of this Citrix NetScaler ADC WAF. The header could be something like X-Forwarded_For.
Import Size Limit (bytes)
cumulative size of all objects imported into Citrix NetScaler ADC. Objects are
- signatures
- WSDLs
- schemas
- HTML error pages
- XML error pages
Citrix NetScaler ADC will rise an error message if you exceed this limit during import. “ERROR: Import failed – exceeding the configured total size limit on the imported objects“. This mainly happens to signatures and HTML error objects containing base64 encoded images.
Learn Messages Rate Limit (messages/second)
The amount of requests and responses per second, the learning engine is allowed to handle. Learning will stop after exceeding this number
Session Time-out (seconds)*
The timeout for idle user sessions. The Citrix NetScaler ADC WAF will discard stored session data (information about cookies, forms, start URL and more) if this timeout is reached. It should be set longer or equal to the longest application timeout. After exeeding this timeout Citrix NetScaler ADC WAF will not accept protected data from this user any more and therefore break the user’s session.
Maximum Session Lifetime (seconds)
The hard way: The time a session may exist, no matter if idle or busy. 0 means: No limit. Users won’t like your limit as it won’t allow normal work, so don’t use it if any possible. It would be like giving a finger salute to users. It’s not usual to set a limit here!
Undefined profile
The profile used if all bound policies evaluate as undefined. This could for example happen if you use http-callout as a policy condition and the callout server is unreachable.
Default profile
The profile used if there is no policy specified to a data stream. This profile is also in general use if you turn on WAF and don’t apply policies.
Session Limit*
If your Citrix NetScaler ADC WAF has to handle more sessions than specified in Session Limit, the applications seems to be frozen. By default this is 100k sessions. The more sessions the Citrix NetScaler ADC WAF has to handle, the more memory it has to spend on storing session data.
The same will happen if you set your limit too high and the Citrix NetScaler ADC goes out of memory.
CEF logging
CEF (Common Event Format) is a machine readable logging format. It’s great if you use scripts to analysis to your logs. It’s also a requirement for Geo Location logging. It’s Turned off by default.
Entity Decoding
Enabling this checkbox tells the Application Firewall to convert any non-ASCII characters into HTML entities before sending a response to the user.
Use Configurable Secret Key
A secret key used in WAF operation. I think, there is a default key built into WAF to be used if you missed to specify a user configured key. This key would be the same all over all Citrix NetScaler ADC WAFs. Unfortunately I could not find documentation about this subject (your feedback would be highly welcome to me).
Geo-Location Logging
I love Geo-Location logging. It explains positive blocks to me. Think of me doing a WAF for a bank, currently busy in India and Sri Lanka. So I would take positives serious coming from India and Sri Lanka, while I’d just skip policy hits coming from Russia or Chile: I’d expect these to be right positives, while Indian positives would probably be false positives.
Geo-Location logging requires CEF-Logging!
Log Malformed Request
Malformed requests get usually dropped silently by Citrix NetScaler ADC WAF. You may force ADC to log these. Keep in mind: This may lead to an enormous amount of log entries during a not well written DDOS attack!
Reset learned data
Last not least, we find the button to reset all learned data here. Learned data is a global CSV file, located in /var/learnt_data. This file is limited in size to 20 MB (not configurable, as far as I know). It may contain up to a bit less than 2,000 learned rules. Learning will stop if this file is filled up. This process is silent. It’s best practice to clear this file prior to start learning for a new vServer, so this file got space enough to be able to keep all newly learned data. This would also avoid confusion with “old data”.
Default profiles
Citrix NetScaler ADC WAF includes some standard profiles:
- APPFW_BYPASS
- APPFW_RESET
- APPFW_DROP
- APPFW_BLOCK
APPFW_BYPASS
These standard profiles contain hardly any settings. A redirect URL may get specified, but it will not be used as this policy hardly blocks anything. Logging all policy hits would cause Citrix NetScaler ADC WAF to also log flawless requests. Allow Semi-colon Form Field Separator would permit ‘;’ as a form field seperator, both in URL queries and POST form bodies. The default setting is off. Secure Credit Card Logging keeps credit card data out of Citrix NetScaler ADC logs. These settings also appear same as in all other Citrix NetScaler ADC WAF profiles profiles.
APPFW_RESET
All settings are simmilar to APPFW_BYPASS, however it sends a TCP reset into the connection, so the browser will show an error page.
APPFW_DROP
Will silently drop the connection, so it would look like there is no server at all. A real hacker would probably understand what’s going on as we could not just successfully establish a TCP connection, but also a TLS session.
APPFW_BLOCK
Blocks requests to the application. Therefore the user will see the configured error page (by default the start page of this website).
How Citrix NetScaler ADC WAF affects requests and responses
Requests
I’m quoting Wikipedia and CTX131488. Some content is mine.
Accept-Encoding
List of acceptable compression methods (GZip, Deflate, …). See HTTP compression. A web application firewall (WAF) would not like a back-end server to send compressed data, as it would need to pass uncompress data to do it’s security scans. In the end the appliance has to recompress data to send compressed traffic to the user. Citrix NetScaler ADC WAF therefore strips Accept-Encoding.
If you compress on server side, your Citrix ADC would have to uncompress all the traffic to do content inspection (credit card and content-type scans) as well as response manipulations like form field consistency and CSRF form tagging scans. So a response would get compressed by your web-server, uncompressed by Citrix ADC and eventually get recompressed after doing all WAF chechs by Citrix ADC. What would this be good for? A total waste of CPU. In the end this would mean some additional degrees of global warming.
Therefore it is best practice, to enable HTTP compression feature together with WAF. This will do the desired compression right after inspection.
Range
Request only part of an entity. Bytes are numbered from 0. See Byte serving. Used to recover from a failed or partial file transfers.
If-Range
If the entity is unchanged, send me the part(s) that I am missing; otherwise, send me the entire new entity. Allows a client to retrieve a partial object when it contains a part of that object in its cache already (conditional GET).
If-Modified-Since
If the requested object is not modified since the time specified in this field, an entity is not returned from the server, instead you will get a 304 Not Modified message. A WAF does not like 304 responses as s a 304 response can’t get inspected and therefore WAF can’t do necessary manipulations to forms.
If-None-Match
Allows a 304 Not Modified to be returned if content is unchanged, see HTTP ETag. Allows efficient updates of cached information with a minimum amount of overhead. A WAF does not like 304 responses as s a 304 can’t get inspected and therefore we can’t do manipulations to forms.
Other request side changes
HTTP/1.1
Citrix NetScaler ADC WAF converts all HTTP/1.0 responses to HTTP/1.1. This is done to avoid unnecessary overhead. HTTP/1.0 always closes server connections while HTTP/1.1 leaves them open. This is not a need from perspective of security, but it is a nice to have.
Response Side
- If Server sends Pragma:no-cache, then the Application Firewall does not do any modification.
- If Client Request is HTTP 1.0, then Application Firewall inserts Pragma:no-cache.
- If Client Request is HTTP 1.1 and has Cache-control: no-store, then Application Firewall does not make any modification.
- If Client Request is HTTP 1.1 and Server Response has Cache-Control header with no store or no cache directive, then Application Firewall does not make any modification.
- If Client Request is HTTP 1.1 and Server Response has either No Cache-control Header or Cache-Control header does not have no store or no-cache directive, the Application Firewall completes the following tasks:
- Inserts Cache-control: max-age=3, must-revalidate,private.
- Inserts X-Cache-Control-orig = Original value of Cache-Control Header.
- Deletes Last-Modified header.
- Replaces Etag.
- Inserts X-Expires-Orig=Original value of the Expire Header sent by the server.
- Modifies the Expires Header and sets the expiration date of the web page to the past, so it is always picked up again.
- Modifies Accept-Ranges and sets it to none.
I hope this is of use to you. I’d be happy to get your remarks and corrections (if needed).
Don’t miss any new blogs: Follow me on twitter @citrix_adc
