last update: November 18th 2019
Hacking nsroot on a NetScaler with default settings is completely easy!
I missed this one in Neil Spelling’s excellent blog about penetration testing NetScalers.
What do you need to hack a NetScaler if you forgot your nsroot password? An external authentication source.
My 1st idea would be: Use nerecover user. But this dies not work, as it uses the same password as nsroot. So I had to dig a bit deeper.
How does NetScaler authentication work?
Well, NetScaler will use any authentication method configured and will check if the username / password pair fits to any authentication method (in order of bindings, lowest number is the highest priority). The last one will always be local authentication. This is done by aaad, the authentication demon.
You may watch this process by opening BSD shell and type cat /tmp/aaad.debug (see here or here)
If aaad is able to authenticate a user it will stop and return a message send_accept sending accept to kernel for : administrator
It will also return a set of groups if there are any. Next step, done by NetScaler itself, is the one we use to exploit the process:
NetScaler will try to find any object matching the user or one of it’s group memberships. So NetScaler will assume this user to be the same as a local user, if it is able to find a user with the same name.
So we got it. We open Active Directory and add an user called nsroot. We give it a password of our own choice. And we will be able to log on.
Panic!
How to fix this issue?
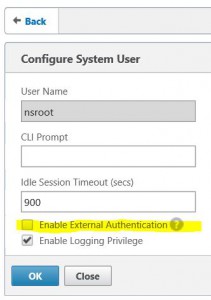
well, let’s open nsroot and disable external authentication. I don’t know why external authentication is enabled for this user, and I’d consider this to be a massive security issue
or simply: set system user nsroot -externalAuth Disabled (Danke Marco Zimmermann)
Have fun

The authentication demon, sounds very dangerous! How the evil like that is allowed to live in inside the NetScalers 🙂
Jani, NetScalers are full of dangerous things. Did you know it also supports even ISIS? Terrorists inside?
[…] “nsroot” with their own password and login with it gaining full admin rights (thanks to Johannes Norz for this […]
This one came to me during normal work.